|
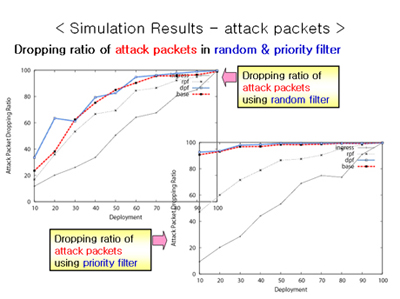
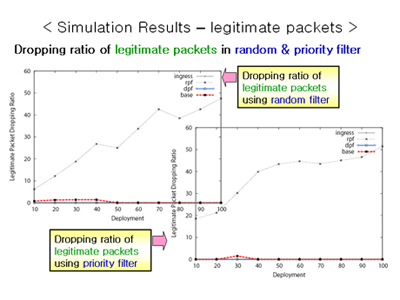
DoS attacks use IP spoofing to forge the source IP address of packets, and thereby hide the identity of the source. This makes it hard to defend against DoS attacks, so IP spoofing will still be used as an aggressive attack mechanism even under distributed attack environment. While many IP spoofing prevention techniques have been proposed, none have achieved widespread real-world use. One main reason is the lack of properties favoring incremental deployment, an essential component for the adoption of new technologies. A viable solution needs to be not only technically sound but also economically acceptable. An incrementally deployable protocol should have three properties: initial benefits for early adopters, incremental benefits for subsequent adopters, and effectiveness under partial deployment. Since no previous anti-spoofing solution satisfies all three of these properties, we propose a new mechanism called "BGP Anti-Spoofing Extension" (BASE). The BASE mechanism is an anti-spoofing protocol designed to fulfill the incremental deployment properties necessary for adoption in current Internet environments. Based on simulations we ran using a model of Internet AS connectivity, BASE shows desirable IP spoofing prevention capabilities under partial deployment. We find that just 30% deployment can drop about 97% of attack packets. Therefore, BASE not only provides adopters' benefit but also outperforms previous anti-spoofing mechanisms.
|
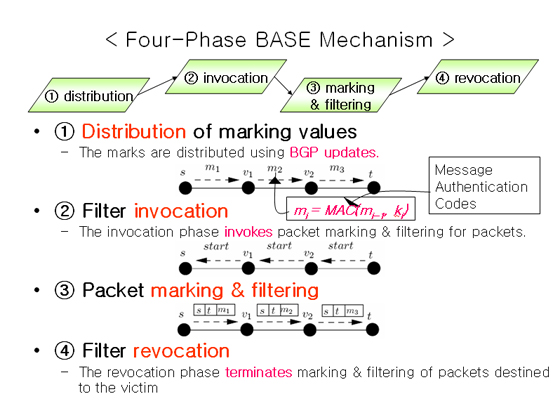
BASE works according to following four phases: distribution of marking values, filter invocation, packet marking and filtering, and filter revocation.
- Phase 1: Distribution of marking values.
The distribution phase is for distributing marking values among BASE filters. The marking value is computed by a one-way hash chain. The marking values are distributed using BGP updates. This is a once-only operation unless the BGP path has been changed.
- Phase 2: Filter invocation.
The invocation phase invokes packet marking and filtering for packets destined to the victim network. Invocation is propagated through BGP update messages. Upon receiving an invocation message, a BASE node starts packet marking and filtering for the corresponding addresses.
- Phase 3: Packet marking and filtering.
The filtering phase marks outgoing packets and filters incoming packets without a correct mark. Every packet with the same source address will have the same mark when it leaves a BASE node, even though it may have arrived with different marks through different interfaces. This replacement scheme allows the BASE mechanism to work in asymmetric routing paths.
- Phase 4: Filter revocation.
The revocation phase terminates marking and filtering of packets destined to the victim. Revocation is also propagated via BGP update messages.
|