|
Defending VoIP Services against Malformed Messages and Flooding Attacks |
|
| Dongwon Seo, Heejo Lee, and Ejovi Nuwere | |
| Abstract | |
|
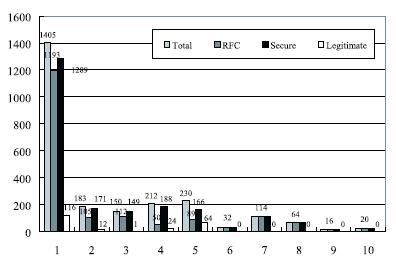
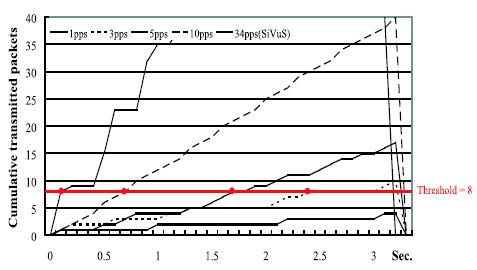
Session Initiation Protocol (SIP) has been used widely for Voice over IP (VoIP) services due to its potential advantages, such as text-based header elds and call setup simplicity. However, SIP-based VoIP services are susceptible to two main attacks: malformed SIP messages and SIP flooding attacks. In this paper, we propose a novel detection mechanism for defending VoIP services against above mentioned security problems. The proposed mechanism consists of two parts: rule matching for detecting malformed messages and a state machine for detecting ooding attacks. As a result, we can detect only 74% of the malformed messages generated by PROTOS, a popular vulnerability assessment tool, when using the rules transformed directly from the RFC speci cation. However, using the improved rules we developed, we can detect 100% of malformed messages in PROTOS. Moreover, it is shown that an adaptive threshold is useful to detect message ooding attacks, while preserving VoIP services. From the experiments on existing ve VoIP services, we show that the proposed mechanism can detect both malformed messages and ooding attacks effectively. |
|
|
Summary |
|
|
To detect SIP attacks, we have designed a detection mechanism, which consists of four parts: malformed SIP detection module, session management, SIP ooding detection and error management module. The most signi cant modules are malformed SIP detection module that includes rule matching algorithm, and SIP ooding detection module that is the combination of four independent state transition algorithms. |
|
 |
|
| Fig.1 The comparison between original rules and secure ones | |
 |
|
| Fig.2 The result of SIP flooding test |